What Is an Anonymous Proxy: Understanding the Key to Online Privacy

As data exposures proliferate in the digital era affecting billions, leveraging anonymous proxies represents a proactive defense granting much-needed obscurity online helping internet users protect sensitive interests across both personal and professional contexts. Below we will explain the essential technologies upholding online privacy.
The Concept of Anonymity Online
At its core, internet anonymity centers around hiding the association between your real-world identity and online activities conducted using digital mediums like browsing websites, posting on forums or accessing services. This breaks potential surveillance, tracking, profiling or blocking by external entities through leveraging intermediate systems like encrypted residential ip address proxy servers that mask actual user IP addresses and other fingerprints websites utilize recognizing individuals behind recurring visits. Anonymity shifts power dynamics towards user interests rather than data hungry platforms.
Goals Fulfilled by Anonymous Proxies
The primary objectives fulfilled by anonymous proxies include:
- 1. Masking real user identity or originating access point hiding details like name, email, geographical location, organization etc that risks tying usage trails to actual individuals without consent.
- 2. Preventing usage pattern tracking, profiling and behavior modeling by external sites based on sites visited, queries made, videos watched since proxies anonymize traffic origin.
- 3. Allowing access to geo-restricted digital content like overseas video libraries, internationally blocked news sites, foreign business journals by spoofing visitor location to sites enforcing regulatory access constraints rather than DRM.
- 4. Facilitating gathering competitive intelligence through responsible data mining initiatives avoiding easy detection and blocklisting by common IP range exposures across marketplaces and forums.
As data weaponization risks accelerate across industries in the absence of regulations, anonymous proxies prove essential for leveling the playing field and securing vulnerable constituent interests.
The Mechanics of Anonymous Proxy Networks
The core technical mechanisms underpinning anonymous internet usage via proxy networks encompass:
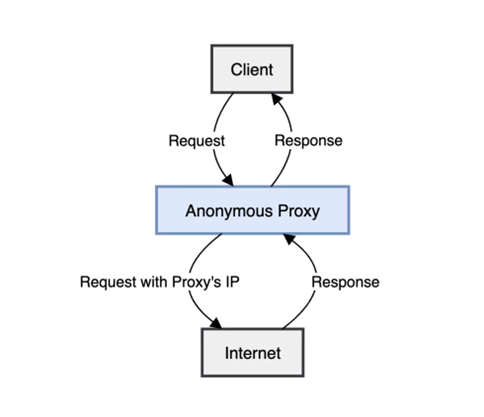
1. Intermediary Routing – Routing of users’ internet traffic first via separate surrogate proxy servers before reaching intended destination sites hides actual visitor IP identity behind proxy IP address.
2. Encrypted Tunneling – Further encrypting entire data flows between user devices and proxies adds additional obscurity through impenetrable data security ensuring no man-in-the-middle interceptions capturing raw traffic and user details.
3. IP Pool Rotation – Employing pools of thousands of frequently changing proxy IP addresses distributing user loads randomly across keeps anonymity across sessions avoiding tracking of usage behavior tied to static IPs which weakens privacy over time.
4. Residential Proxies – Utilizing proxies based out of authentic residential ISP assigned IP addresses rather than data centers better mimics real home internet usage evading advanced threat detection.
5. Custom Client Software – Specialized client applications simplify securely activating then randomly hopping between encrypting anonymous residential proxy nodes across countries and subnets maximizing online anonymity with ease.
Thus by synergizing critical privacy and security technologies codified into best practice frameworks, anonymous proxies offer a versatile positive-impact mechanism upholding essential user safeguards rapidly eroding across cyberspace.

Classes of Anonymous Proxies by Strength
However, anonymizing capabilities vary based on technology robustness across proxy sub-types:
1. Elite Proxies – Top tier IP pools utilize military-grade encryption, true residential IPs, real-time IP cycling, custom client apps and other advanced features maximizing anonymity for the most sensitive applications.
2. Commercial Proxies – Mainstream proxy services offer solid mid-grade infrastructure, encryption and IP refreshing suited for daily privacy preservation and geo-arbitrage access needs for commercial usage rather than state-level threats.
3. Public Proxies – Free publicly available proxies generally offer subpar inconsistent uptime, risky security from lack of encryption safeguards and easily traced static IP exposures given extremely high usage volumes concentration. Resort if needed for basic personal interests or trial evaluation.
Not all proxies live up to anonymity claims equally. Vet quality characteristics before applying for irreplaceable user data guarding.
Read Also: 6 Useful IoT Software Solutions Your Business May Need
Typical Usage Scenarios Enabled by Anonymous Proxies
Commonly encountered online situations where activating anonymous proxies better upholds positive user interests include:
1. Public WiFi Hotspot Usage – Masking identity, location and usage tracking risks from open WiFi monitoring or hackers intercepting transmission via proxies adds vital security for conducting any sensitive activities like financial transactions, login sessions etc while on the go leveraging transport free internet access.
2. Accessing Overseas Digital Content Sites – Leverage geo-spoofing capabilities switching assigned proxy IP locations to designated countries for unlocking world class overseas media sites geo-blocked locally due to dated licensing bureaucracy rather than piracy risks. Experience global internet access freedoms where personal usage causes no loss.
3. Responsible Web Scraping Initiatives – For well-intentioned professional web scraping data mining engagements needing large volumes. Frequently alternating residential proxy IPs avoids fast detection vs company IPs easily blocked limiting project success. Carefully vet ethics.
4. Discreet Market Research Around Sensitive Niche Use Cases – For both personal and professional interests involving researching socially difficult topics like medical conditions, sexuality issues, substance addiction and more where anonymity encourages open inquiry free of stigma or profiling risks by external platforms or ISPs that hold broadband monopolies. Treat access as privileged empowerment responsibly upholding public goodwill.
Conclusion
The above examples demonstrate legitimate applications where anonymous proxies strengthen positive outcomes for internet users faced with increasing data vulnerabilities from profit-driven global platforms lacking sufficient choice or safeguards currently. Anonymity proves pivotal for leveling the strategic playing field back towards public interests until formal policy catches up to technology adoption realities.