What is Tor Browser, and Who Uses It?

The concern about being secure and safe has risen because of the increasing population of the global online community. Some netizens may stick to managing their online activity, while others go a step further. This concern overtakes all types of VPNs and browsers like the Tor Browser. Its features are compatible with providing users with fully secure internet browsing.
The Tor Browser is one of the most efficient privacy tools that delivers users secure internet browsing. In this article, we will provide a comprehensive overview of the browser, its uses, workings, and potential shortcomings.
Tor Browser – An Overview
The Tor Browser is an open-source browser designed to provide users with options to have anonymous browsing. The term Tor stands for The Onion Router and refers to how the browser encrypts its communication channels. Apart from being free, it is also decentralized and runs its relays all because of volunteers from around the globe.
On its surface, it acts like any other browser. Apple’s ecosystem doesn’t support it, but you can install the browser on a Windows PC, Linux, or Android. Websites have mechanisms to know if traffic comes from the Browser and they may block such traffic. However, the advantages of this platform outweigh the drawbacks for some users.
The Tor Browser Pros and Cons
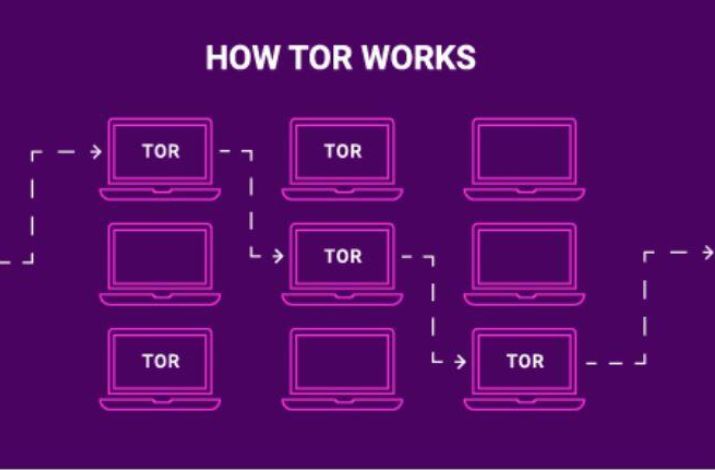
How Does Tor Bowser Work?
The Tor Browser secures anonymity by encrypting users’ connections. Each time you want to access content on the internet, it heavily encrypts your connection. It then directs it through three layers of relays (hence the onion analogy), picking a random one on its network every time.
Each relay decrypts one of the three encryption layers before accessing the desired site. Someone monitoring your internet activity could surmise you’ve been using this Browser. However, they wouldn’t be able to tell what you’ve been using it for.
Since it has to go through three “checkpoints” each time you need to visit a website, it is noticeably slower than regular browsers. It also offers several security layers, like disabling JavaScript or media content on the sites you visit, which can make the experience even slower.
Why Use the Tor Browser?
If you are concerned about your privacy more than anything, you can use the Tor Browser to make your identity anonymous. While its capabilities make it part of criminals’ toolkits, ordinary people with neutral or good intentions make up the largest part of its user base.
If you don’t want your ISP or government to know what you’re doing on the internet; however harmless it might be. Others, like whistleblowers, journalists, and activists, use it to fight oppression in areas of the world where free speech is undesirable.
It is perfectly legal for citizens in developed democracies. More authoritarian regimes ban or block it as a means of reinforcing censorship. The browser’s development is ongoing, so it’s possible to circumvent such bans in the upcoming days.
What’s the Difference Between the Tor Browser and a VPN?
After knowing such knowledge about the Tor Browser, you may have a question; what is the difference between a VPN and this browser?
The main difference is that Tor Browser encrypts only your browsing activities, while a VPN secures your entire internet connection. It includes streaming services, game servers, torrent trackers, and more. VPNs emphasize end-point security and protect communication from theft and cyberattacks to provide users with useful security.
Sometimes VPNs offer additional features, and turning the same VPN on can protect you from online threats or help you block malware. That means this tool, for the most part, is specifically designed to enhance users’ security for better protection.
Moreover, using a VPN doesn’t slow down your browsing experience as much as the Tor Browser since the tunnel that encrypts communication is a single protective measure. It uses random relays, meaning that the IP address a website sees will also be random. VPNs may cycle through IP addresses, but you can specify your location whether in your country or abroad.
The Tor Browser is completely free for users all over the world. Companies develop VPNs and offer their most powerful features to users through paid subscriptions. This gives them a vested interest in keeping their products updated and capable of shielding you from a wide range of cyberattacks.
The Tor Browser and the Dark Web
The Dark or Deep Web refers to online websites search engines don’t index. Combine that with the ability to visit such sites anonymously, and it’s clear why this Browser is the perfect browser to access such no-index sites.
Among other things, the dark web is home to illegal and immoral content that we highly encourage you not to pursue. For some, it’s also the only means by which they can communicate freely, expose injustice, and organize to do something about injustice.
Tor Browser Features
For those who are willing to make use of this browser at its peak, we have compiled a list of its features. Here are some of the Tor Browser features.
- Go Anywhere: Users can access the Tor Browser on Linux, Windows, and Mac.
- Ultimate Protection: Your data will be converted into a secret code before it travels the web.
- Double in One: Enjoy the best of Firefox and the Tor Project combined.
- Stay Hidden: Websites won’t know who’s visiting – it’s a secret between you and the Tor Browser.
- Unlock Everything: It gets you into blocked and no-index websites.
- Source Incognito: Whatever you do, your IP address stays a secret.
- Beyond Boundaries: Breakthrough firewalls and reach hidden online places.
- Handling the Load: Thousands of relays, millions of users – it can take it all.
Closing Thoughts
The Tor Browser is a must-have in today’s world where freedom of speech is so low because of several issues. Further, if your workplace restricts certain websites, and you need to keep your online activities private from prying eyes or the NSA, it is your go-to solution. While it offers potent anonymous browsing capabilities, it’s not flawless. Its browsing speed can be a tad slow, and vulnerabilities can surface. Plus, be mindful that using it might draw undesired attention from your government or internet service provider.
FAQs
Q1- What is the Tor Browser used for?
The Tor browser, for instance, is used by many reporters in countries where freedom of expression is restricted so that they can cover controversial themes while remaining anonymous.
Q2- Where can I download Tor?
The Tor Browser can be installed through the Tor Project’s website. Tor’s installation on both Windows and Mac is fairly similar and simple.
Q3- Does Tor hide my IP address?
The answer to this question is yes. The Tor Browser has the ability to hide your IP address from other websites.
Q4- Will anyone know what have you done on Tor?
Sometimes, if your internet service providers continuously track you, they may know you were on Tor Browser. Fortunately, they are unable to know what you have done on that browser.
Q5- Does Tor Browser delete your browsing history?
Yes, the Tor Browser delete your browsing history immediately when you return from that platform.






