2 days ago
Guide to Use AI to Invest in Crypto and Manage Your Portfolio
Using AI to invest in crypto and manage your portfolio proved unimaginably helpful. We all know that crypto trading will…
2 days ago
How to Write Quality Content Based on E-A-T for your Business?
Writing quality content for your business is essential for growth as it delivers value to your customers. The standard of…
2 days ago
Basics of Oil Trading: Futures, Options, and ETFs
Imagine navigating the volatile seas of oil trading, where understanding the instruments of futures, options, and ETFs is like mastering…
3 days ago
How to Schedule Google My Business Posts Effectively
Creating a Google My Business (GMB) profile is crucial for businesses of all niches in today’s digital era. GMB enables…
3 days ago
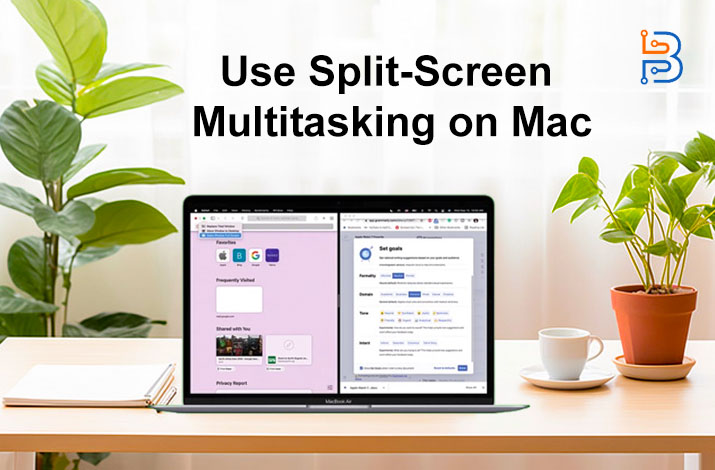
How to Use Split-Screen Multitasking on Mac?
Split-screen multitasking on Mac is gaining the significance it deserves because it helps users improve their efficiency. It allows users…